 Around the Ides of March, Google (following in Facebook’s footsteps) banned all cryptocurrency advertising, effective June 2018. Crowdfund Insider reported that in 2017 alone Google blocked 3.2 billion ads from its platform. Now Chrome has added to its Developer Program Policies a ban that prohibits products that “mine cryptocurrency” from its Web Store in order to stave off cryptojacking. Existing extensions that mine cryptocurrency will be delisted from the Chrome Web Store in late June.
Around the Ides of March, Google (following in Facebook’s footsteps) banned all cryptocurrency advertising, effective June 2018. Crowdfund Insider reported that in 2017 alone Google blocked 3.2 billion ads from its platform. Now Chrome has added to its Developer Program Policies a ban that prohibits products that “mine cryptocurrency” from its Web Store in order to stave off cryptojacking. Existing extensions that mine cryptocurrency will be delisted from the Chrome Web Store in late June.
“As the extensions ecosystem continues to evolve, we remain focused on empowering developers to build innovative experiences while keeping our users as safe as possible. Over the past few months, there has been a rise in malicious extensions that appear to provide useful functionality on the surface, while embedding hidden cryptocurrency mining scripts that run in the background without the user’s consent,” blogged Google Extensions Platform Product Manager James Wagner. “These mining scripts often consume significant CPU resources, and can severely impact system performance and power consumption.”
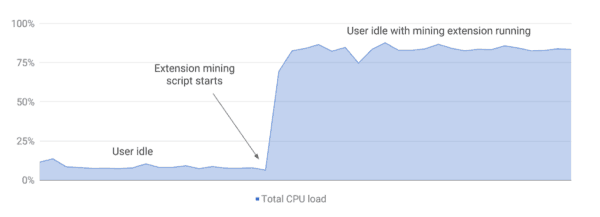
Wagner indicated that the extensions with other types of blockchain-related functionality will still be permitted.
“Unfortunately, approximately 90% of all extensions with mining scripts that developers have attempted to upload to Chrome Web Store have failed to comply with these policies, and have been either rejected or removed from the store,” added Wagner.
[clickToTweet tweet=”.@Google Chrome has banned products that mine #cryptocurrency from its Web Store in order to stave off cryptojacking.” quote=”@Google Chrome has banned products that mine #cryptocurrency from its Web Store in order to stave off cryptojacking.”]
Cryptojacking’s surge has coincided with the rise with cryptocurrency’s boom, but what is cryptojacking?
 “Cryptojacking can be used for legitimate purposes, like raising revenue for a publishing platform or collecting funds for charitable causes. But in practice, the technology has largely been implemented maliciously, or at least secretly, consuming processing resources on victim devices and potentially interfering with and damaging these targets,” explained Wired Security Staff Writer Lily Hay Newman. “Bad actors can use locally installed malware to steal a victim device’s computing power, embed miners directly into websites to target casual web users without needing to install anything, or hide miners in the most innocuous applets and tools.”
“Cryptojacking can be used for legitimate purposes, like raising revenue for a publishing platform or collecting funds for charitable causes. But in practice, the technology has largely been implemented maliciously, or at least secretly, consuming processing resources on victim devices and potentially interfering with and damaging these targets,” explained Wired Security Staff Writer Lily Hay Newman. “Bad actors can use locally installed malware to steal a victim device’s computing power, embed miners directly into websites to target casual web users without needing to install anything, or hide miners in the most innocuous applets and tools.”

