Yesterday, Ledger and their internal hack team Ledger Donjon, published a highly critical blog post targeting Trezor and their cryptocurrency wallets. The post highlighted multiple vulnerabilities regarding the Trezor products where devices could be hacked. One of the identified issues was deemed “unable to patch.”
Today, Trezor has responded to the claims in a blog post of their own.
Trezor stated that none of the vulnerabilities could be exploited remotely as a hacker would have to have physical access for an attack. Additionally, the mission of hardware wallets is to:
“..protect users and funds against malware attacks, computer viruses, and various other remote dangers (like stealing all funds from Ledger via the Stealth Change Address).” [emphasis added]
The TDLR version is here:
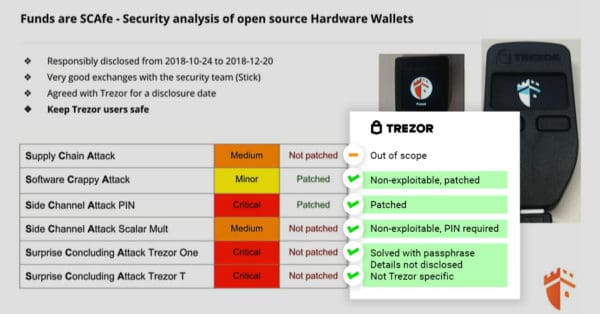
- Supply Chain Attack: Out-of-scope, affects all hardware in transport, no 100% solution, all companies have different methods to mitigate this
- Software Crappy Attack: Non-exploitable, patched
- Side Channel PIN Attack: Patched
- Side Channel Attack Scalar Multiplication: Non-exploitable, PIN required
- Surprise Concluding Attack: Not disclosed fully, implications for all hardware devices based on ST microchips, mitigated by passphrase
Trezor also provided an updated image defending their products against Ledger’s claims.
You can read the dust-up here.